 Free Keylogger
Free Keylogger
Concerned About Your Children Safety?
If your kids spend time chatting or playing computer games, they can be approached or threatened by the strangers. Internet has anonymity, and anonymity means impunity in the minds of molesters. The solution? Violate their anonymity by monitoring your kids' activities!
REFOG Free Keylogger is designed to deal with extended families, but it fits small families just as easy. Allowing you to monitor your children activities remotely over the Internet, REFOG Free Keylogger does not even require your close presence in order to be alerted about suspicious activities of either your children or someone they chat with.
Easy To Install and To Use
REFOG can be set up and used by anyone. The monitor does not involve a steep learning curve and does not demand a degree in Computer Science to configure and operate. Simply download your free trial version and get yourself going!
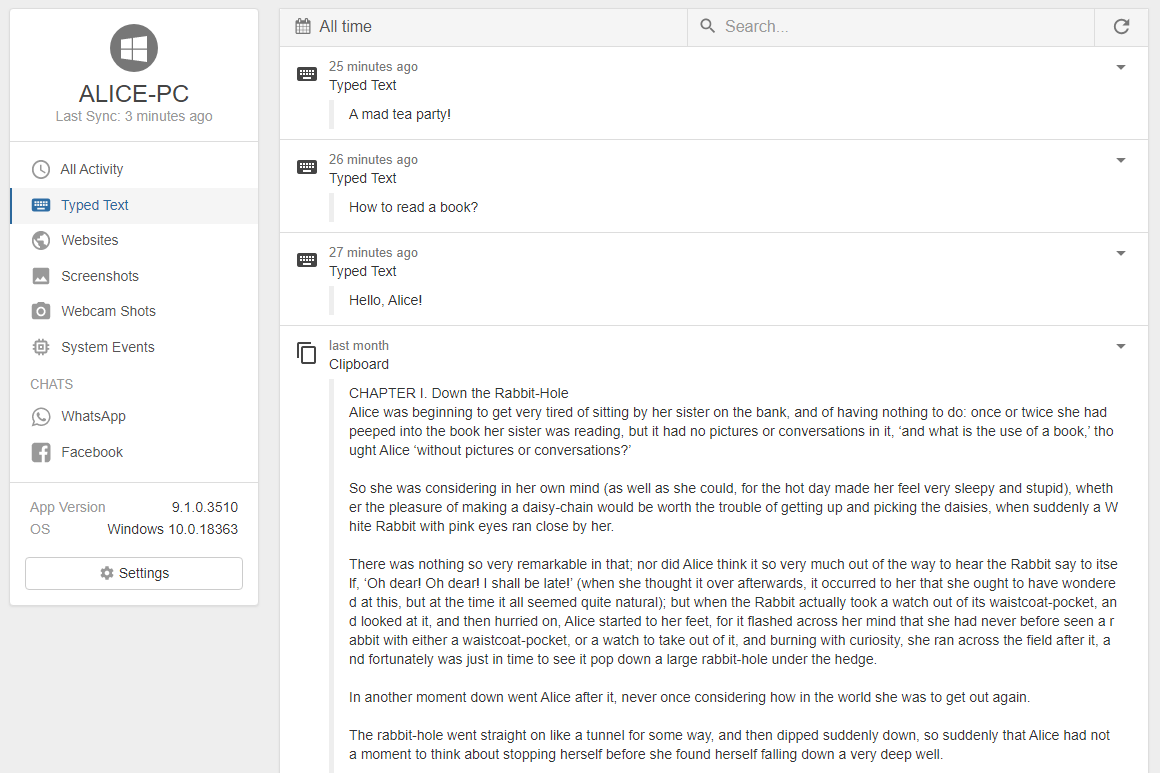
Save Screens and Key Presses
REFOG keeps a list of all activities you specify it to log. It records all visited Web sites, keeps logs of chats and instant messenger conversations as well as other things typed or received by your kids in chats, messengers, blogs, forums and other online and offline applications.
REFOG saves each key pressed and every phrase typed, and makes periodic captures of the computer screen to better illustrate what was going on at that moment.
Capture Chats and Instant Messengers
REFOG captures every key that they press, but does not stop there. Individual keystrokes are of little use when analyzing your kids' behavior. REFOG software can detect popular chats and instant messengers, and forms clearly legible and readable logs containing chats and instant messenger conversations formatted in a manner that is convenient to read.
Stealth Operation
For even better protection, REFOG Free Keylogger can be completely hidden from your kids' eyes. It runs silently and unobtrusively on their PC while taking screen shots and recording every key that they press, logging applications that they use and Web sites that they visit.
Use Refog to:
- Log all keystrokes while staying completely invisible for users
- Log all text fragments copied to the clipboard